The Latest from Boing Boing |  |
- Eliza: what makes you think I'm a psychotherapeutic chatbot?
- Jargon Watch: Infovegans versus Cookie Monsters
- FBI steals Instapaper servers
- LulzSec leaks Arizona law enforcement papers (Updated with excerpts)
- Bell-dummy for training pickpockets
- Taiwan: Blogger fined $7K, jailed for 30 days over negative noodle review
- Choosing strong passwords: promise and peril
- High-tech venture capitalists to Congress: The PROTECT IP Act is bad for America
- This could be inspiring, or the set up for a joke. You pick.
- Antibiotic resistance: It's more than just staph
- Pervious concrete is awesome, kind of zen
- A somewhat useful data logging of a years' worth of meals
- Mara Hvistendahl responds to Richard Dawkins' BB guest-post on science and sex selection
- Why study brain injuries in a comic book?
- Electronic traffic sign warns of zombies!
- Belarus: KGB goes after activists through their social media accounts
- Inside an abandoned coal power plant (photos from Boing Boing Flickr Pool)
- Fukushima babies and how numbers can lie
- Major US ISPs set to limit repeat infringers with throttling, limiting access to 200 websites, and copyright reeducation school
- Model net neutrality rule for municipalities
- Campus hookups: college sex isn't new, but hookups are different
- Palin denies quitting bus tour
- Why fair use doesn't work unless you've got a huge war-chest for paying lawyers
- Abandoned Australian Deco power-station, rusting and covered in graffiti
- Happy Birthday, Alan Turing
- Pentax Q
- University of Michigan to stop worrying about lawsuits, start releasing orphan works
- Phone-tree navigator waits on hold for you
- A Brief History of the Corporation: understanding what an attention economy is and where it comes from
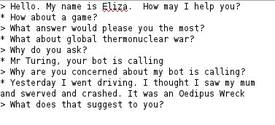
| Eliza: what makes you think I'm a psychotherapeutic chatbot? Posted: 24 Jun 2011 03:31 AM PDT In a three-part history of the Eliza psychotherapeutic chatbot, Jimmy Maher ('the digital antiquarian') covers both the circumstances of Eliza's birth and the way that the people around her thought about her. The third installment, in particular, deals with the reactions of people who watched people reacting to Eliza -- that is, what do we make of the way that Eliza's creator felt about the way that Eliza's users behaved: Eliza, Part 1 (via O'Reilly Radar) (Image: NLP Addiction) |
| Jargon Watch: Infovegans versus Cookie Monsters Posted: 24 Jun 2011 03:07 AM PDT  Two coinages from my Twitter feed this morning: Two coinages from my Twitter feed this morning: Infovegan: One who refuses cookies (@cjoh via @carlmalamud -- see infovegan.org for more) Cookie Monster: One who accepts cookies (JMike2) (Image: Cookie Monster, a Creative Commons Attribution (2.0) image from nickstone333's photostream) |
| Posted: 23 Jun 2011 08:55 PM PDT The FBI, acting on a warrant, seized an internet scam ring's servers—and, apparently, those of everyone else in the datacenter rack. Among the victims of Operation Go Go Gadget Cybercrime Investigation was Instapaper, Marco Arment's splendid and widely-used web bookmarking system. Due to the police culture in the United States, especially at the federal level, I don't expect to ever get an explanation for this, have the server or its data returned, or be reimbursed for the damage they have illegally caused. I'm really not sure what to do about this. I'm speaking to my lawyer about it shortly, but as far as I know, there's nothing I can reasonably do without spending more money, time, and stress than I can afford on a path that would likely lead nowhere productive.The FBI stole an Instapaper server in an unrelated raid [Instapaper] Update: The server's back online, Arment reports. |
| LulzSec leaks Arizona law enforcement papers (Updated with excerpts) Posted: 23 Jun 2011 09:01 PM PDT LulzSec announced Thursday evening the publication at Pirate Bay of a trove of leaked material from Arizona law enforcement agencies. Arizona's Department of Public Safety confirmed shortly thereafter that it was hacked. In the press release included with the dump, a LulzSec affiliate outlines a more activist agenda than is usually associated with the group. With more than 700 bulletins, email archives, images and other files, the 440MB package will keep readers busy for days. A few excerpts from the most obviously newsworthy documents follow. Amid countless AZDPS emails covering subjects ranging from internal training, policies, events and goings-on in the criminal underground, this remarkable circular: "BELOW ARE PICTURES TAKEN AFTER A RAID ON A DRUG DEALER'S HOUSE IN MEXICO. ARE YOU READY FOR THIS???AREN'T WE GLAD THAT WE HAVE AN OPEN BORDER POLICY BETWEEN US? JUST LOOK AT HOW WELL ITS PAYING OFF........ I THINK ALLOWING MEXICAN TRUCKERS IN THE U.S. IS A GREAT IDEA!!! JUST TAKE A LOOK AT THE MILLIONS OF REASONS WHY......... SEE HOW WELL THESE TRUCKERS ARE DOING? WHAT THE @#@%*@ ARE WE THINKING??? Notice that nearly 100% of this money is U.S. Currency!!! Do you now wonder why the cost of living has catapulted in our country??? I don't...... Some of the illegal aliens we're letting in can afford anything at any cost!!! And for the ones who cannot........ We'll give it to them anyway!!!AND WE HAVE TWO BORDER PATROL AGENTS IN PRISON FOR SHOOTING AND WOUNDING A WELL DOCUMENTED MEXICAN DRUG DEALER! WHO, BY THE WAY, WAS ARMED AND ALSO HAPPENS TO BE A CONVICTED (BY MEXICO) MURDERER . MAKES A LOT OF SENSE, DOESN'T IT??? AUTOMATICS, SILENCERS...... THEY'RE ALL HAVING A NICE LAUGH ABOUT THIS STUFF AT OUR EXPENSE!!! And we want to give ILLEGAL ALIENS amnesty and not build the border fence because of funding!?!?!? SEND THIS TO EVERYONE, INCLUDING YOUR LOCAL CONGRESS REPRESENTATIVE. Our country is bleeding from the outside in!!! Don't you think it's time we take back what WE have sacrificed for over 140 years for??? I do. Build the fence higher and deeper, tighten border control, and send EVERY illegal alien home!!!" In another email, there's discussion of the Mexican government using recently-bought radio gear to intercept U.S. communications: "The FBI asked the Mexican Government to sign an "Intercept Agreement" stating that they would not use these devices to listen to U.S. Government radio traffic, and the Mexican Government declined to sign the agreement. The implication is that obviously the Mexican Government intends to do a lot of listening." There are countless mundane documents covering hours worked, officers' personal information and other stuff of minimal journalistic interest. But the bulletins often offer fascinating stories of law enforcement encounters, such as this one with off-duty Marines patrolling the U.S.-Mexico border with assault weapons. "In other incidents reported in October, U.S. Border Patrol agents encountered two subjects who claimed to be members of the Border Watch Group the Blue Lights based on the Caballo Loco Ranch. The subjects, armed with pistols and at least one M4 rifle, were dressed in full desert camouflage uniforms, similar to those of the United States military. They stated they were not members of the Minutemen, but paid contract employees who "get the job done" and "were not just volunteers". They possessed valid United States Marine Corps identification cards." Among the documents exposed by LulzSec is a PowerPoint presentation of the vulnerabilities of ferries to terrorist attack, a report of 'suspicious incident trends' in Arizona; and a review of a homebrew chemical weapon recipe found online: "DHS and the FBI assess that improvised "chlorine bombs" constructed using plastic soda bottles containing pool treatment tablets mixed with rubbing alcohol based on instructions found on the Internet pose a minimal toxic hazard." On Twitter, Nigel Parry spots a report on iPhone apps that "cops hate: Cop Recorder, Police Alert Lite, Trapster; Caller ID Faker, digital scale" There appears to be a problem in Arizona (think of the sun!) with officers doing awful touch-up jobs on their interceptors: "Crown Vic Paint Issues-If a vehicle doesn't qualify for paint replacement, a district may purchase primer, spray paint and sandpaper to attempt to improve vehicle appearance. This must be closely monitored by district commanders as I assured Lt. Col. ... that we would not make the vehicles look worse than they do now. If you have someone in the district with some skills in this area, consider utilizing them for quality assurance." Particularly interesting are the Arizona Counter Terrorism Information Center "high-capacity flash memory devices are becoming increasingly concealable making them difficult for law enforcement officials to detect and identify during searches. Data can then be stored on these devices and then transferred between the concealed USB device and an external device, such as a computer, via a modified USB cable."USB flash drives are being produced and disguised as jewelry, pens, lip balm containers, cigarette lighters, wristbands, poker chips, credit cards, calculators, multi-purpose utility knives, emergency medical pill containers, lanyards, a wide variety of children's toys, and other inconspicuous items." But not all are so high-tech, with one bulletin describing an apparently failed "Hotel Room Burglary Tool" made with wire and foil. Drug traffickers are using GPS to do battle; smugglers are using scouts on horseback to evade U.S. authorities. "Arizona law enforcement officials have learned that multiple groups, including several Drug Trafficking Organizations (DTOs), are using available GPS technology to target rivals. DTOs are placing GPS tracking devices on load vehicles of their rivals to reveal stash house locations, in order conduct home invasions raids to steal drugs and money on a later date." Smuggler scouts "may utilize high-rise vantage points, travel the same roads repeatedly, serve as decoys, hide in bushes, and, in one case, used horses in their efforts to locate and identify law enforcement." Some Arizona Department of Public Safety computers remain on dial-up: "The dial-up internet connection is extremely slow and inconsistent, .06 megabits per second. There are often two officers sharing this slow connection, which makes for even slower speeds and less consistent service. Some of the videos on the intranet and training sites are five, ten or even fifty megabytes, which means it often takes from four to twenty hours to download some of the videos and files necessary for training or other work related items" The spice must not flow! Recent information developed by the Patrol Division has indicated "powder" forms of the chemical components of the substance known as "spice" have been ordered over the internet (primarily from overseas sources) and possibly shipped to local post office boxes. The chemical components of "spice" are diluted in water to form a paste like substance and then applied to regular cigarettes; after drying, the cigarettes could be smoked to gain the effect of the "spice". Upon casual observation, this method of ingestion would make it appear that individuals would be smoking regular cigarettes. ... Officers should exercise extreme caution when handling regular cigarettes; the "spice" solution would be water soluble and easily absorbed through bare skin on contact. Officers should pay attention to regular cigarettes for the possibility of "spice" contamination and be aware of any potential criminal activity. In one document, titled "A NEW BREED OF SUSPECT," the author reports the existence of tactical guides for criminals labeled, "23 rules for winning shootouts with police." Also in the dump is AOL's guide for law enforcement who need to file subpoenas, and an intriguing look at the presence of Outlaw Motorcycle Gangs and the military: Through our extensive investigation, it has been discovered that many of these OMG members were not only retired or inactive military, but were also continuing their training and/or careers as Government contractors on military installations and Federal buildings throughout the United States and abroad. Furthermore, ATF OSII will be discussing the relationship between military-associated clubs and OMGs. On several occasions, both groups have been observed riding side by side and attending the same events and motorcycle runs. In one memo, authorities determined that the "Threat level" posed by "Jews for Jesus" was low! I'm sure they'll be happy to hear it. There are a great many BOLO-type mugshots and bios for wanted suspects; LulzSec's latest release represents the greatest single concentration of incompetent tattoos in recorded history. One brief advises law enforcement officers on how to prevent people using the "Find my iPhone" feature to wipe cellphones remotely: Law enforcement seizing iPhones as potential evidence are recommended to protect the phone from wireless signals as soon as possible through the use of a faraday bags or some other nickel, copper and silver plated storage container. The device must be protected from any wireless connection/radio signal even throughout the forensic imaging process. A "COUNTER-TERRORISM INFORMATION CENTER" bulletin sees fit to cover domestic civil rights protests, but points out that "There is no credible information to indicate there is concern for public safety. Despite the potential disruptive nature of these events, officers should be cognizant of the protestors' First Amendment Rights." Here's an excerpt from the report on iPhone apps that can be "used against officers," in which they are advised to "take the time to look at an arrestee's cell phone to see what applications they have." Cop Recorder: This can be activated while in a pocket and record everything the officer is saying. When activated it gives a warning statement to the user, which is basically the Miranda rights and advises against talking to an officer until they speak to an attorney. One document is titled "shootout at a McDonalds," authored by "a California Sergeant."
"You cannot have the typical police mind-set in an off-duty situation," concludes the sergeant who so artfully avoided saying who fired first in a shootout in the presence of children. " ... I was really worried that one of my own guys might not recognize me. I was worried too that there might be some other off-duty copper around who would think I was the bad guy." A guide to social networking sites cautions officers not to boast about beating arrestees on Facebook, because that may be of use to defense attorneys: One of the notable postings introduced to the jury was that the officer watched the movie "Training Day" (a motion picture that displayed corrupt police behavior and brutality) to brush up on "proper police procedure. One of his postings said, "If he wanted to tune him up some, he should have delayed cuffing him." In another he added, "If you were going to hit a cuffed suspect, at least get your money's worth 'cause now he's going to get disciplined for a relatively light punch." Another memo describes the appearance and pseudonyms of Purple Drank, "a recreational drug popular in the hip-hop community>" slang terms for purple drank include: "Sizzurp, Lean, Syrup, Drank, Barre, Purple Tonic, Southern Lean, Texas Tea, Memphis Mud, Mrs. Dranklesworth, Tsikuni, Lean, P-Flav, Slip, Purple Sprite, PG Tips, Purp, and Purple Jelly". The generic prescription name is Phenergan. A report on racial profiling concludes that "Even after controlling for other explanatory factors, racial/ethnic disparities exist for warnings, repair orders, citations, arrests and seaches. ... Further analyses of searches and seizures illustrate that hispanic, black and native american drivers were significantly more likely to be searched compared to whites." A "Parents' Guide to Internet Lingo" decodes all that leet umadbro jellyspeak the youngsters converse in these days. "A/S/L" comes in at 11 on the top 20. An unclassified but FOIA-exempt report discloses that a source of "undetermined reliability" claimed Al-Qaeda "planned to carry out an attack using suicide operatives against unspecified business centers and subways throughout the United States. The attack would incorporate automatic weapons."
First, the suspect moved the cuffs in front of him. He then pulled off the rubber weather stripping on the frame of the car and removed the inside door panel, exposing the door locking mechanism. He stuck his finger in between the door and the frame and released the latch opening the door.It took the defendant all of a few minutes to perform the escape. Officers apprehended him a few blocks away.
|
| Bell-dummy for training pickpockets Posted: 23 Jun 2011 02:32 AM PDT  The Feb, 1930 issue of Modern Mechanix carried a story about Scaltiel, a stage-performer whose act revolved around picking pockets. Scaltiel claimed to have learned his trade after being inducted into a guild of pickpockets who tested him on a "bell-dummy" whose every pocket "was wired so that the slightest touch would result in the ringing of a bell, showing that the amateur thief was clumsy." Sometimes a thief will go to great lengths to "contact" his victim. He will drop a glove under the seat of some innocent party without being seen. Then the thief will retrieve the glove and offer it to his victim who believes that some polite person has made a mistake. He will speak to the thief, unaware that while he is looking at the thief, the nimble fingers are exploring his pockets or extracting a stick pin or "lifting" a watch. The thief is holding out the glove with his right hand while his left "mit" is at work.Amateur PICK POCKETS Study in CRIME College |
| Taiwan: Blogger fined $7K, jailed for 30 days over negative noodle review Posted: 23 Jun 2011 03:26 PM PDT  (Photo: a delicious plate of noodles in Toronto by John Elmslie, contributed to the Boing Boing Flickr Pool.) A court in Taiwan this week ruled against a female food-blogger who said a local restaurant's beef noodles "were too salty," and that she'd seen cockroaches scurrying around in the restaurant. She gets 30 days in detention, two years of probation, and must pay 200,000 Taiwanese dollars (about $7K US dollars) in compensation to the restaurant. The court didn't argue she was lying about the bugs, but ruled that "Ms. Liu should not have criticized all the restaurant's food as too salty because she only had one dish on her single visit." After visiting a Taichung beef noodle restaurant in July 2008, where she had dried noodles and side dishes, Liu wrote that the restaurant served food that was too salty, the place was unsanitary because there were cockroaches and that the owner was a "bully" because he let customers park their cars haphazardly, leading to traffic jams. The restaurant owner, who sounds like a total dick (I can say this because I'm not in Taiwan!), said "he hoped the case would teach her a lesson."
Again, from the Taipei Times:
(via LA Weekly) |
| Choosing strong passwords: promise and peril Posted: 22 Jun 2011 10:15 PM PDT The Agile Bits blog discusses good methods for choosing a human-memorable "master password" that is used to lock up a file of non-memorable, strong passwords: Toward Better Master Passwords (via JWZ) (Image: Change your password or the dog gets it, a Creative Commons Attribution Share-Alike (2.0) image from dnisbet's photostream) |
| High-tech venture capitalists to Congress: The PROTECT IP Act is bad for America Posted: 23 Jun 2011 01:09 PM PDT A reader writes: "Fifty-four venture capitalists from forty firms sent a letter to one hundred Senators and a number of Congressman expressing concern about S. 968, the PROTECT IP Act ('PIPA'), which would allow rights-holders to require third-parties to block access to and take away revenues sources for online services, with limited oversight and due process. The signatories to this letter work for firms that manage over $13B. We are early investors in services like Facebook, Twitter, Zynga, Skype, Groupon, LinkedIn, Tumblr, Foursquare, and a host of other important web services. The services they have backed now reach over a billion users." |
| This could be inspiring, or the set up for a joke. You pick. Posted: 23 Jun 2011 01:02 PM PDT |
| Antibiotic resistance: It's more than just staph Posted: 23 Jun 2011 12:54 PM PDT Here's something that really is killing kids: A new strain of scarlet fever that's about twice as resistant to antibiotics as previous antibiotic-resistant strains. This is heart-wrenching. My thoughts are with the families in Hong Kong suffering through this outbreak. |
| Pervious concrete is awesome, kind of zen Posted: 23 Jun 2011 12:48 PM PDT Pervious concrete is, basically, just concrete that allows water to flow through it. This has some benefits and detriments for urban environments, as explained on NPR's Science Friday. Frankly, though, it's kind of pleasant to just sit back and watch this patch of pervious concrete absorb 1500 gallons in five minutes. |
| A somewhat useful data logging of a years' worth of meals Posted: 23 Jun 2011 12:18 PM PDT One woman documented her meals for a year and turned them into a series of data visualizations. What did I learn? Well, for one thing, how important it is to gather and group data into logical and easily comparable categories. For another, this woman ate more french fries than fruit. (Via Liz Landau) |
| Mara Hvistendahl responds to Richard Dawkins' BB guest-post on science and sex selection Posted: 23 Jun 2011 12:18 PM PDT Richard Dawkins contributed a guest post to Boing Boing over the weekend, sparked by a piece in the Guardian about Mara Hvistendahl's book, Unnatural Selection. "I am responding to allegations made by Richard Dawkins that my book is critical of science," Hvistendahl writes in a response post on her blog. "It is not." |
| Why study brain injuries in a comic book? Posted: 23 Jun 2011 06:11 PM PDT  Last week, I told you about a new, peer-reviewed study detailing more than 700 cases of traumatic brain injury in the comic Asterix. Yesterday, I went on New Hampshire Public Radio's Word of Mouth to talk about WHY that study was done. That's the question everybody had about this research. And it's a reasonable question. After all, what good is it to anyone to know how comic book characters get injured? The answer is surprising. On several levels. For one thing, lead author Marcel Kamp told me that Traumatic brain injuries in illustrated literature: Experience from a series of over 700 head injuries in the Asterix comic books is the first peer-reviewed paper he's ever published that didn't need any revisions. The reviewers were very supportive, right from the beginning. The other big surprise: This is really a culture shock thing. Turns out, what the general public sees as frivolous "dumb science" makes a lot more sense if you know how this paper fits into the cultural norms of medical research. I explain this in my Word of Mouth interview, but I will spoil you on one little tidbit. Before you complain about the waste of public funds, you really should know that no public funds were spent on this paper. As Kamp told me, "the analysis" was done on weekends and holidays, using the researchers own collections of comic books. Image: goldenslumbus, a Creative Commons Attribution Share-Alike (2.0) image from terrapin_flyer's photostream |
| Electronic traffic sign warns of zombies! Posted: 23 Jun 2011 12:10 PM PDT  Highway contractors kindly deployed this electronic road sign last night in northern Kentucky. Unfortunately, the Kentucky Transportation Cabinet thought it to be a practical joke. They'll learn soon enough once drivers start disappearing. "Interstate 71/75 sign warns of zombies" (Cincinnati.com, thanks Charles Pescovitz!)
|
| Belarus: KGB goes after activists through their social media accounts Posted: 23 Jun 2011 12:12 PM PDT AP: "Belarus is undergoing a severe economic crisis, and longtime President Alexander Lukashenko has overseen a sweeping crackdown on opposition and government critics. Authorities routinely block opposition websites using web-filters similar to those used in China. Pro-democracy activists such as those protesting Wednesday routinely use Facebook, Twitter and other social networking websites to support one another and their cause." But one activist says he was arrested this week and only released after he agreed to give the KGB his social media account passwords. |
| Inside an abandoned coal power plant (photos from Boing Boing Flickr Pool) Posted: 23 Jun 2011 11:58 AM PDT  Photographer and Boing Boing reader Tom Blackwell shot a wonderful series of images from a visit to an abandoned coal power plant in the UK: the Thorpe Marsh Power Station. He shared them with us in the BB Flickr pool, and explains about the image above:
A few more below, with Tom's notes. Do have a look at the whole set in his Flickr stream.
The crumbling skeleton of this coal-fired giant sits broodingly in low lying fields to the north of Doncaster. The story of Thorpe Marsh Power Station began with its construction in 1959, amid much fanfare heralding its advanced generators and state-of-the-art component technologies.
Cooling towers are cast in a hyperboloid shape, which make for some fun perspectives when photographing them. They also generate some incredible echos inside. It was a very windy day when I visited Thorpe Marsh and the rustling of some old debris at the base of the tower turned into a crescendo of loud whispers which was very eerie indeed. Have a look at this image to see how these structures appear during construction.
All of the towers at the abandoned Thorpe Marsh Power Station are equipped with one of these tiny doorways peeking out from the sheer concrete drop, about a quarter of the way up. They used to provide access to a central inspection walkway over the grid of pipework and cooling equipment in the bottom level. For a sense of scale, one of these doorways can be seen cut into a place near the top of a tower in the lower left of this photograph.
The calling card of an old British industrial manufacturer which was founded in 1918 and largely disbanded in 1968. Old logos and brands are always valued by photographers in abandoned places - they make a great comment on the transient nature of commercialism when you see a powerful company of the past reduced to an obituary in the form of a rusty plaque.
This shed could once be considered the mouth of the power station. When running smoothly, this hungry beast could consume well over half a million tonnes of coal per year so it was important to have consistent and continuous supply. Railway vehicles known as hoppers would roll over the large pits beneath these rails and shed their load of coal to stock up the fuel reserves and keep Yorkshire's light bulbs burning brightly.
|
| Fukushima babies and how numbers can lie Posted: 23 Jun 2011 11:53 AM PDT  Xeni brought this to my attention yesterday. Over at Scientific American, Michael Moyer takes a critical look at an Al Jazeera story about a recent study purporting to show that infant deaths on the American West Coast increased by 35% as a result of fallout from the Fukushima Daiichi nuclear power plant meltdown. At first glance, the story looks credible. And scary. The information comes from a physician, Janette Sherman MD, and epidemiologist Joseph Mangano, who got their data from the Centers for Disease Control and Prevention's Morbidity and Mortality Weekly Reports—a newsletter that frequently helps public health officials spot trends in death and illness. Look closer, though, and the credibility vanishes. For one thing, this isn't a formal scientific study and Sherman and Mangano didn't publish their findings in a peer-reviewed journal, or even on a science blog. Instead, all of this comes from an essay the two wrote for Counter Punch, a political newsletter. And when Sci Am's Moyer holds that essay up to the standards of scientific research, its scary conclusions fall apart.
You can see that data all plotted out nicely by Moyer over at Sci Am. How did these numbers get so heinously distorted? It's hard to say. But there should be some important lessons here. In particular, this is a good reminder that human beings do not always behave the way some economists think we do. We're not totally rational creatures. And profit motive is not the only factor driving our choices. When you think about what information be skeptical of, that decision can't begin and end with "corporate interests." Yes, those sources often give you bad information. But bad information comes from other places, too. The Fukushima accident was worse than TEPCO wanted people to believe when it first happened. Radiation isn't healthy for you, and there are people (plant workers, emergency crews, people who lived nearby) who will be dealing with the effects of Fukushima for years to come. But the fact that all of that is true does not mean that we should uncritically accept it when somebody says that radiation from Fukushima is killing babies in the United States. Just because the corporate interests are in the wrong doesn't mean that every claim against them is true. Reality leaves us in a confusing place. As Slacktivist, one of my favorite bloggers, likes to say, "It's more complicated than that." With "it," in this case, meaning "everything." The best solution is to always ask questions, even when the people we're questioning look like the good guys. Image: Baby toes, a Creative Commons Attribution (2.0) image from 40765798@N00's photostream |
| Posted: 23 Jun 2011 10:51 AM PDT Four of the largest ISPs in the USA are on the verge of approving a deal with the RIAA and MPAA that'll require ISPs to limit people who repeatedly infringe copyright to visiting only 200 websites, throttled bandwidth, and/or sending them to copyright re-education school. These are characterized as an alternative to outright disconnection, but as the entertainment execs behind it know that heavily throttled connections or limited access to a small collection of websites are tantamount to disconnection when it comes to the diverse benefits accrue to Internet users. And being sent to a copyright school designed by the entertainment industry isn't likely to deliver a decent understanding of education. After years of negotiations, a group of bandwidth providers that includes AT&T, Comcast, and Verizon are closer than ever to striking a deal with media and entertainment companies that would call for them to establish new and tougher punishments for customers who refuse to stop using their networks to pirate films, music and other intellectual property, multiple sources told CNET.Exclusive: Top ISPs poised to adopt graduated response to piracy (via Ars Technica) |
| Model net neutrality rule for municipalities Posted: 22 Jun 2011 11:47 PM PDT  Jeff sez, "Recently, Boing Boing shared our post suggesting that local communities could take inspiration from Pittsburgh's City Council ban on fracking and make net neutrality law, instead of waiting for Congress. Working with CELDF, the author of the Pittsburgh law, Envision Seattle has authored a model ordinance to legislate Net Neutrality . This post contains the first draft of the model net neutrality ordinance which we will ask the Seattle City Council to pass. We encourage other communities to study the ordinance and adopt it in their own jurisdictions. Our ordinance is meant to be used as a template for municipalities around the U.S. and globally as a starting point in codifying their right to a free and open Internet. p.s. Today, the Netherlands became the first European country to make Net Neutrality law." The Seattle City Council and the people of Seattle find that access to the broadband internet creates opportunity for more direct civic engagement and increased educational attainment and free speech; and that such access enables people to more fully participate in a democratic process. To date, the network design principles fostering the development of the broadband internet - an end-to-end design, layered architecture, and open standards - promote innovation at the edge of the network and gives end users choice and control of their online activities.Model Net Neutrality Ordinance for Seattle (Thanks, Jeff!) (Image: Net Neutrality News Tag Cloud, a Creative Commons Attribution Share-Alike (2.0) image from seanweigoldferguson's photostream) |
| Campus hookups: college sex isn't new, but hookups are different Posted: 22 Jun 2011 11:37 PM PDT Lisa Wade, a sociology prof at Occidental College, presented a talk on "The Promise and Perils of Hook-Up Culture" at Franklin & Marshall College, explaining her research findings in a survey of students' attitudes to casual sex on campus. She affirms that casual sex on campus is nothing new, but that the "hookup culture"'s expectations and demands are a serious impediment to sexual and emotional happiness: In her own research, Lisa has found that students want sex to be pleasurable, empowering, or meaningful. But, alas, they seem to have difficulty achieving any one of those things in great measure. The culprit, she concludes, isn't hooking up, it's hook up culture. When a hook up culture dominates, all other ways of being sexual are repressed, and that leaves many students involuntarily celibate or having sex they don't really want. The solution: an opening up of sexual options that allow students to truly, genuinely explore their own sexualities safely."The Promise and Perils of Hook-Up Culture" |
| Palin denies quitting bus tour Posted: 23 Jun 2011 07:40 AM PDT A reminder of one of the differences between Sarah Palin and Michelle Bachmann illustrated in the Matt Taibbi piece Xeni linked to yesterday: Bachmann is a natural political campaigner, whereas Palin is not. [Jezebel] |
| Why fair use doesn't work unless you've got a huge war-chest for paying lawyers Posted: 23 Jun 2011 07:27 AM PDT  Last year, Waxy released Kind of Bloop, a chiptunes tribute to Miles Davis's Kind of Blue. He meticulously cleared all the samples on the album, and released it for $5 (backers of his Kickstarter project got it for free -- Waxy is founder of Kickstarter). One thing Waxy didn't clear was the pixellated re-creation of the iconic cover photo he commissioned. He believed and believes that it is fair use -- a transformative use with minimal taking that doesn't harm the market for the original, produced to comment on the original. Jay Maisel, the photographer who shot the original, disagreed, and sued Waxy for $150,000 per download, plus $25,000. Waxy ended up settling for $32,500, even though he believes he's in the right -- he couldn't afford to defend himself in court. He's written an excellent post on copyright, fair use, and the way that the system fails to protect the people who are supposed to get an exception to copyright: In practice, none of this matters. If you're borrowing inspiration from any copyrighted material, even if it seems clear to you that your use is transformational, you're in danger. If your use is commercial and/or potentially objectionable, seek permission (though there's no guarantee it'll be granted) or be prepared to defend yourself in court.Kind of Screwed |
| Abandoned Australian Deco power-station, rusting and covered in graffiti Posted: 23 Jun 2011 07:50 AM PDT  Abandoned Journey visited Fremantle Power Station, a giant, rusting Art Deco building in Australia on the Indian Ocean. The graffitied ruins are spectacular. Much of the complex is rusting and rotting beyond any salvation, and quite dangerous to explore. The four major chimney stacks have been demolished, leaving a huge gaping holes throughout the complex. This allows rain to get in, which is the worst nightmare for any building trying to remain standing. Combined with the seaside location, and the local winds, the future for the abandoned Power Station is very predictable - mother nature has begun it's relentless reclamation. The daily winds are so reliable and regular in nature, the locals have actually named the breeze the "Fremantle Doctor". As in, "the Doctor is blowing hard today". We explored the complex extensively, and it became apparent that in some areas, we were probably taking far too great a risk. The rusting metal overhead walk-ways did not seem stable at all.Abandoned 1940's Power Station - Urban Exploration Photos | ABANDONED JOURNEY (Thanks, Dr. Hank Snaffler Jr.!) |
| Posted: 23 Jun 2011 07:10 AM PDT Today is Alan Turing's birthday. Happy birthday, old bean! Thanks for all the crypto and the foundations of modern computing and the seminal AI work. Sorry about the bigots who murdered you. (Thanks, dr.hypercube!) |
| Posted: 23 Jun 2011 07:22 AM PDT  Pentax's Q has similar looks to rangefinder-style digicams from Fujifulm and Leica, but is smaller and, at $800, less expensive. Like Micro 4/3 and NEX models in that bracket, it has interchangeable lenses—with five on offer and a 47mm-equivalent, f1.9 lens bundled with the body. A major caveat, however, is its 1/2.3" sensor, which puts the spec sheet closer to cheap point-and-shoot models a third of its price. It'll be out in the fall. [Pentax] Pentax's Q has similar looks to rangefinder-style digicams from Fujifulm and Leica, but is smaller and, at $800, less expensive. Like Micro 4/3 and NEX models in that bracket, it has interchangeable lenses—with five on offer and a 47mm-equivalent, f1.9 lens bundled with the body. A major caveat, however, is its 1/2.3" sensor, which puts the spec sheet closer to cheap point-and-shoot models a third of its price. It'll be out in the fall. [Pentax] |
| University of Michigan to stop worrying about lawsuits, start releasing orphan works Posted: 23 Jun 2011 07:09 AM PDT Bobbyg sez, "The University of Michigan Library will be sharing digital copies of their orphan works, that is, copyrighted works which have no identifiable owner, with the University community. Paul Courant, the University Librarian, says that the project is integral to the mission of the library, and that the sharing of the orphan works is a 'fair use' of the material, stating that 'sharing these orphan works does no economic harm to any person or organization, while not doing so harms scholarship and learning...'" Orphan Works Project (Thanks, Bobbyg!) |
| Phone-tree navigator waits on hold for you Posted: 23 Jun 2011 07:03 AM PDT Fonolo automates navigating stupid, complex corporate phone menus: browse through its maps of large companies' menu-systems, decide which department you want to speak to, and give it your phone number. It calls the company, navigates to the appropriate spot, and waits on the hold queue until it reaches a human, then calls you and bridges you in. They use online forms to gather the information the person on the phone is going to ask you and transmit it to her/him. I don't know how secure or private the system is, but it's basically what I've wanted since the first time I encountered a hold-queue (if it works, I'll even forgive them "cloud-based" and "voice 2.0" buzzword-compliance). (via /.) |
| Posted: 22 Jun 2011 10:31 PM PDT Venkatesh Rao's tour-de-force blog-post, "A Brief History of the Corporation: 1600 to 2100," is an attempt to synthesize several accounts of economic trends and the institutions that fuel and benefit from them, primarily corporations. Beginning with the age of mercantilism and the East India Company's many bubbles and busts (not to mention ruthless conquests and brutal consolidations); Rao moves onto the "Schumpeterian" era where growth was driven by innovation and the "colonization of time" in the form of "labor-saving" devices that let corporations capture more value from their workers. Rao concludes with a brief section on the current era, the "Coasean" period in which individuals, coordinating among each other, are at center stage -- basically, maker culture. Part history lesson, part economic speculation, Rao's essay is provocative, a little esoteric, well-written and challenging. A Brief History of the Corporation: 1600 to 2100 (via Futurismic) (Image: Red Wing Shoes Factory Tour, a Creative Commons Attribution (2.0) image from 94693506@N00's photostream) |
| You are subscribed to email updates from Boing Boing To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |

 Weizenbaum's reaction to all of this has become almost as famous as the Eliza program itself. When he saw people like his secretary engaging in lengthy heart-to-hearts with Eliza, it... well, it freaked him the hell out. The phenomenon Weizenbaum was observing was later dubbed "the Eliza effect" by Shelly Turkle, which she defined as the tendency "to project our feelings onto objects and to treat things as though they were people." In computer science and new media circles, the Eliza effect has become shorthand for a user's tendency to assume based on its surface properties that a program is much more sophisticated, much more intelligent, than it really is. Weizenbaum came to see this as not just personally disturbing but as dangerous to the very social fabric, an influence that threatened the ties that bind us together and, indeed, potentially threatened our very humanity. Weizenbaum's view, in stark contrast to those of people like Marvin Minsky and John McCarthy at MIT's own Artificial Intelligence Laboratory, was that human intelligence, with its affective, intuitive qualities, could never be duplicated by the machinery of computing -- and that we tried to do so at our peril. Ten years on from Eliza, he laid out his ideas in his magnum opus, Computer Power and Human Reason, a strong push-back against the digital utopianism that dominated in many computing circles at the time.
Weizenbaum's reaction to all of this has become almost as famous as the Eliza program itself. When he saw people like his secretary engaging in lengthy heart-to-hearts with Eliza, it... well, it freaked him the hell out. The phenomenon Weizenbaum was observing was later dubbed "the Eliza effect" by Shelly Turkle, which she defined as the tendency "to project our feelings onto objects and to treat things as though they were people." In computer science and new media circles, the Eliza effect has become shorthand for a user's tendency to assume based on its surface properties that a program is much more sophisticated, much more intelligent, than it really is. Weizenbaum came to see this as not just personally disturbing but as dangerous to the very social fabric, an influence that threatened the ties that bind us together and, indeed, potentially threatened our very humanity. Weizenbaum's view, in stark contrast to those of people like Marvin Minsky and John McCarthy at MIT's own Artificial Intelligence Laboratory, was that human intelligence, with its affective, intuitive qualities, could never be duplicated by the machinery of computing -- and that we tried to do so at our peril. Ten years on from Eliza, he laid out his ideas in his magnum opus, Computer Power and Human Reason, a strong push-back against the digital utopianism that dominated in many computing circles at the time.  We are releasing hundreds of private intelligence bulletins, training manuals, personal email correspondence, names, phone numbers, addresses and passwords belonging to Arizona law enforcement. We are targeting AZDPS specifically because we are against SB1070 and the racial profiling anti-immigrant police state that is Arizona. The documents classified as "law enforcement sensitive", "not for public distribution", and "for official use only" are primarily related to border patrol and counter-terrorism operations and describe the use of informants to infiltrate various gangs, cartels, motorcycle clubs, Nazi groups, and protest movements. Every week we plan on releasing more classified documents and embarassing personal details of military and law enforcement in an effort not just to reveal their racist and corrupt nature but to purposefully sabotage their efforts to terrorize communities fighting an unjust "war on drugs". Hackers of the world are uniting and taking direct action against our common oppressors - the government, corporations, police, and militaries of the world. See you again real soon! ;D
We are releasing hundreds of private intelligence bulletins, training manuals, personal email correspondence, names, phone numbers, addresses and passwords belonging to Arizona law enforcement. We are targeting AZDPS specifically because we are against SB1070 and the racial profiling anti-immigrant police state that is Arizona. The documents classified as "law enforcement sensitive", "not for public distribution", and "for official use only" are primarily related to border patrol and counter-terrorism operations and describe the use of informants to infiltrate various gangs, cartels, motorcycle clubs, Nazi groups, and protest movements. Every week we plan on releasing more classified documents and embarassing personal details of military and law enforcement in an effort not just to reveal their racist and corrupt nature but to purposefully sabotage their efforts to terrorize communities fighting an unjust "war on drugs". Hackers of the world are uniting and taking direct action against our common oppressors - the government, corporations, police, and militaries of the world. See you again real soon! ;D  Avoid secrets or things that are personally meaningful
Avoid secrets or things that are personally meaningful 








 The Orphan Works Project is being led by the Copyright Office of the University of Michigan Library to identify orphan works. Orphan works are books that are subject to copyright but whose copyright holders cannot be identified or contacted. Our immediate focus is on digital books held by HathiTrust, a partnership of major research institutions and libraries working to ensure that the cultural record is preserved and accessible long into the future.
The Orphan Works Project is being led by the Copyright Office of the University of Michigan Library to identify orphan works. Orphan works are books that are subject to copyright but whose copyright holders cannot be identified or contacted. Our immediate focus is on digital books held by HathiTrust, a partnership of major research institutions and libraries working to ensure that the cultural record is preserved and accessible long into the future.  Take an average housewife, the target of much time mining early in the 20th century. It was clear where her attention was directed. Laundry, cooking, walking to the well for water, cleaning, were all obvious attention sinks. Washing machines, kitchen appliances, plumbing and vacuum cleaners helped free up a lot of that attention, which was then immediately directed (as corporate-captive attention) to magazines and television.
Take an average housewife, the target of much time mining early in the 20th century. It was clear where her attention was directed. Laundry, cooking, walking to the well for water, cleaning, were all obvious attention sinks. Washing machines, kitchen appliances, plumbing and vacuum cleaners helped free up a lot of that attention, which was then immediately directed (as corporate-captive attention) to magazines and television.
No comments:
Post a Comment